When running a digital classroom, you connect with millions of students worldwide.
But how do you protect their data?
Lucky for you, we’ve talked to some leading experts in edtech security and data privacy.
And they have some amazing tips and best practices. These tips will keep your students safe and secure in the ever-changing edtech world.
So, let’s dive in.
Why are edtech security and data privacy so important to your business?
Let’s discuss why security and data privacy are so important for your edtech business.
Here are a few reasons:
- Your users trust you with their personal information. So, protecting their privacy is essential.
- You can lose your reputation and customers if a data breach happens.
- You’re responsible for complying with data privacy. You should also follow laws and regulations like COPPA and GDPR.
- Cyberattacks are rising, and education businesses are a prime target.
- Protecting students’ data can help you gain a competitive edge and win their trust.
What are the common challenges in edtech security and protecting student data?
Protecting student data is no easy feat. And your edtech company may face several challenges when keeping users’ data safe.
Here are a few of the most common challenges you may encounter:
- The sheer volume of data: You collect and store massive amounts of data. This makes data security difficult to manage and secure.
- Third-party providers: You may rely on third-party providers. You’ll need services like data storage and analytics. This can create more security risks.
- Human error: Despite robust security measures, human error can still cause data breaches. For example, your employees could share sensitive information by mistake.
- Lack of resources: Small edtech may lack the resources. They don’t invest in the latest security measures. They may not also hire dedicated security professionals.
- Compliance: Edtech companies should follow a variety of data privacy. And regulations, including COPPA and GDPR. This can be complex and time-consuming.
What are the common threats and vulnerabilities in education technology?
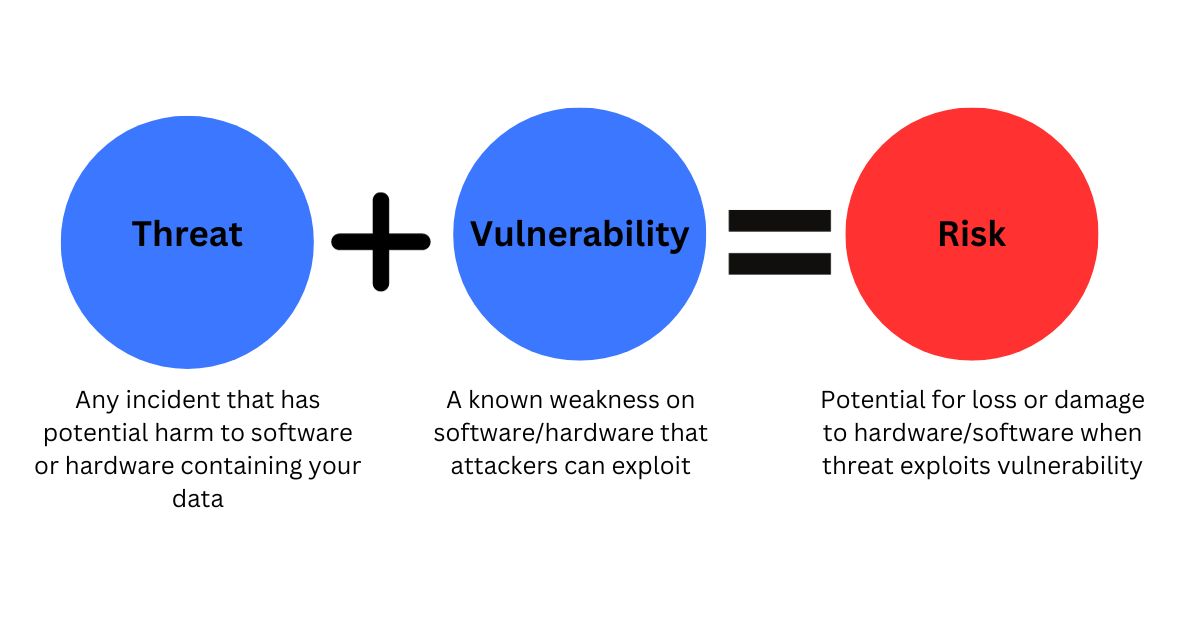
As an edtech company, you must know the cybersecurity threats that could risk your users’ data.
Here are some of the most common threats and vulnerabilities to watch out for.
1. Phishing attacks
Phishing attacks are like baited hooks. Hackers use these hooks to trick you into giving away your sensitive information.
In edtech, these attacks are usually aimed at students and teachers.
The hackers send fake emails. They can also build fake websites that look like the real thing to steal login credentials.
2. Ransomware
Ransomware is malware that can lock you out of your files.
The hackers then ask for payment for the key to unlock them.
Edtech companies are prime targets for ransomware attacks. They often store sensitive data and may be more willing to pay the ransom to avoid data loss.
3. Social engineering
Social engineering is the use of tricks and tactics. Hackers use these tricks to get sensitive information through deception.
In Edtech, hackers might impersonate someone you trust.
This includes a teacher or administrator. Once they gain your trust, the next target is to gain access to your data.
4. Data breaches
Data breaches happen when someone accesses or steals sensitive information without permission.
How is your edtech at risk? When someone gains unauthorised access to confidential information.
This information could include student records, financial information, or identifiable information.
5. Malware
Malware is software that harms your device or steals your sensitive information.
Malware attacks can wreak havoc on your edtech company’s devices, networks, and data.
In the context of edtech, malware can take various forms.
This includes viruses, worms, trojans, ransomware, and spyware.
These malicious programs can spread through infected downloads, email attachments, or websites.
Now that you know some common threats and vulnerabilities, let’s discover how to prevent them.
A step-by-step guide on how to prevent edtech security breaches and data theft
Securing your edtech business from cyber threats can seem daunting. But taking the right steps can make all the difference.
Here’s a step-by-step guide to help you prevent security breaches and data theft.
Step 1: Conduct a security audit
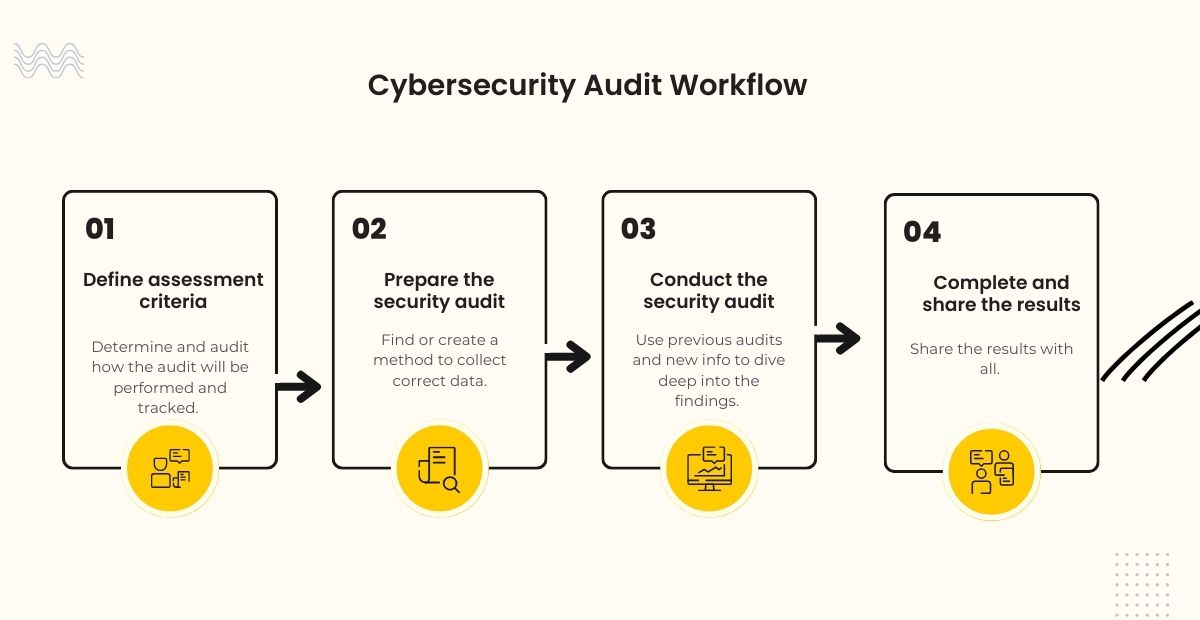
Doug Levin, the mastermind behind EdTech Strategies, has some excellent advice for us.
“Before anything else, conduct a thorough security audit to uncover vulnerabilities. And understand the risks in your edtech environment.”
Sounds important? But where do you even begin?
No worries, We’ve got you covered. Follow these steps in the security audit workflow:
- Define your goals: Start by setting clear goals for the audit. What do you want to achieve? Identify the areas you want to assess and improve security.
- Prioritise and set success criteria: Determine what success looks like for each goal. Prioritise and establish criteria to measure your progress.
- Dive deep into findings: Use previous audit reports and gather new information. Examine your systems, processes, and controls to identify vulnerabilities or weaknesses.
- Share the results: Share the findings with your team once you’ve completed the audit. This ensures everyone understands the current security status.
- Take action: Based on the audit findings, create a list of action items. Assign responsibilities and set deadlines to keep everyone accountable.
Now you’re on your way to bolstering your edtech security. And protecting your digital classroom.
But how do you educate your users about security and data privacy?
This brings us to our next step.
Step 2: Educate your users

You know what’s essential?
Educating your students and staff about online safety. Make them understand how to spot and handle potential threats.
Founder of PlayWell LLC, Linnette Attai, says, “User education is the key”.
So, make sure you take the time to teach your students and staff about staying safe online. Teach them to protect their privacy and be smart regarding cyber threats.
It’s about equipping them with secure digital navigation knowledge and skills.
To start with educating your users, take inspiration from the following examples:
- Develop training programs.
- Provide resources that educate students and teachers about cybersecurity.
- Teach students and teachers about how to create strong passwords. Avoid phishing scams and secure personal devices.
Step 3: Implement access controls
Listen to Dr. Justin Patchin, the co-director of the Cyberbullying Research Center.
According to Dr Justin, having access controls in place is super important.
You must control who can get their hands on your sensitive data. And ensure only authorised people have access to it.
That makes sense, right? Now, let’s get practical with an example.
Here’s what you can do to implement access controls:
- Use user authentication: Set up unique usernames and strong passwords for everyone so that they can access your edtech system. This way, you ensure that only the right folks can get in.
- Use multi-factor authentication: Consider using multi-factor authentication. This means users must provide more than just a password to gain access. It could be a fingerprint scan or a one-time verification code sent to their mobile device.
So keep those sneaky intruders at bay. And have a strong grip on who can access your sensitive data.
Step 4: Use encryption
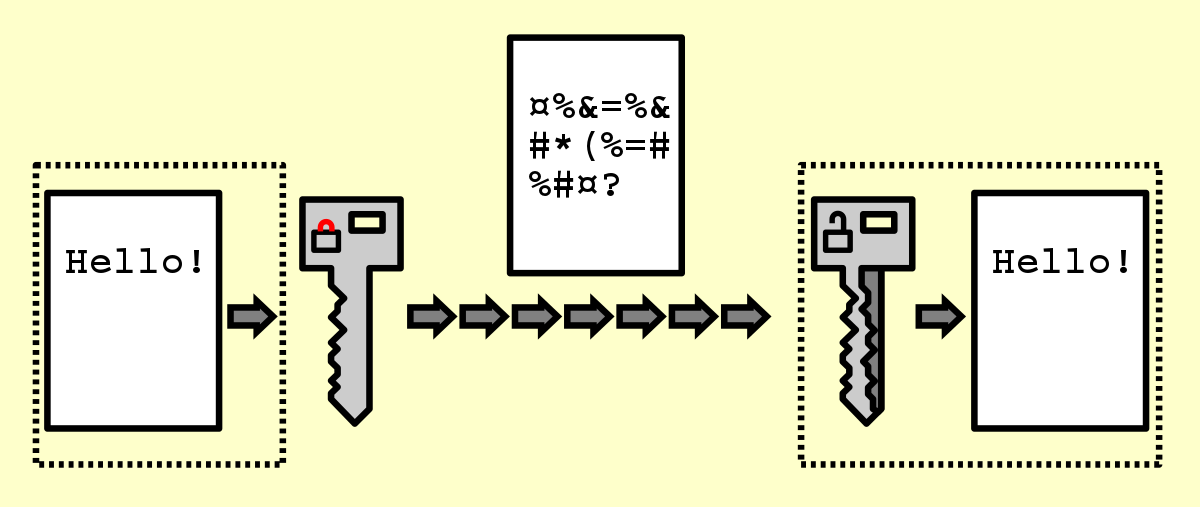
Milda Macenaite, the cybersecurity expert, specialises in encryption.
Milda says it’s super important to encrypt sensitive data to keep it safe. Whether it’s moving around or just chilling on a device.
Now, let’s get down to business with an example.
Check out these cool ways you can use encryption:
- Protect data in transit: Data travels between users, devices, or servers. Ensure it’s shielded with encryption. That way, even if someone intercepts it, they won’t be able to make sense of it. It’s like sending your data on a top-secret mission.
- Secure stored files: Don’t forget those sensitive files stored on your devices. Encrypt them to add an extra layer of protection. It’s like locking them up in a secret vault only you can access.
So, be the encryption hero of your edtech world by following this advice and examples.
Your sensitive data will be like a fortress, impenetrable to prying eyes.
Step 5: Implement security software
Shannon Tabaldo is the Senior Director of Product Management at GoGuardian. Shannon has some solid advice for you.
Shannon says you must invest in heavy-duty security software to lock your digital classroom down.
Now, let’s get into the nitty-gritty with an example.
Check out these excellent security software options:
- Use antivirus software: Install reputable antivirus software. And give that pesky malware and viruses a big “NOPE.” It’s like having a superhero guardian that scans and removes any digital baddies lurking around.
- Build a strong firewall: Set up a firewall to act as a protective shield around your digital classroom. It keeps unauthorised access and your precious data safe and sound. It’s like having a virtual bouncer that keeps the troublemakers at bay.
- Get intrusion detection systems: Get yourself an intrusion detection system. And spot any suspicious activity in your digital realm. It’s like having a watchful eye that alerts you when something fishy happens.
Remember, it’s not just about installing these tools. You must stay on top of things. Regularly update and maintain them to stay one step ahead of emerging threats.
Step 6: Plan for incidents
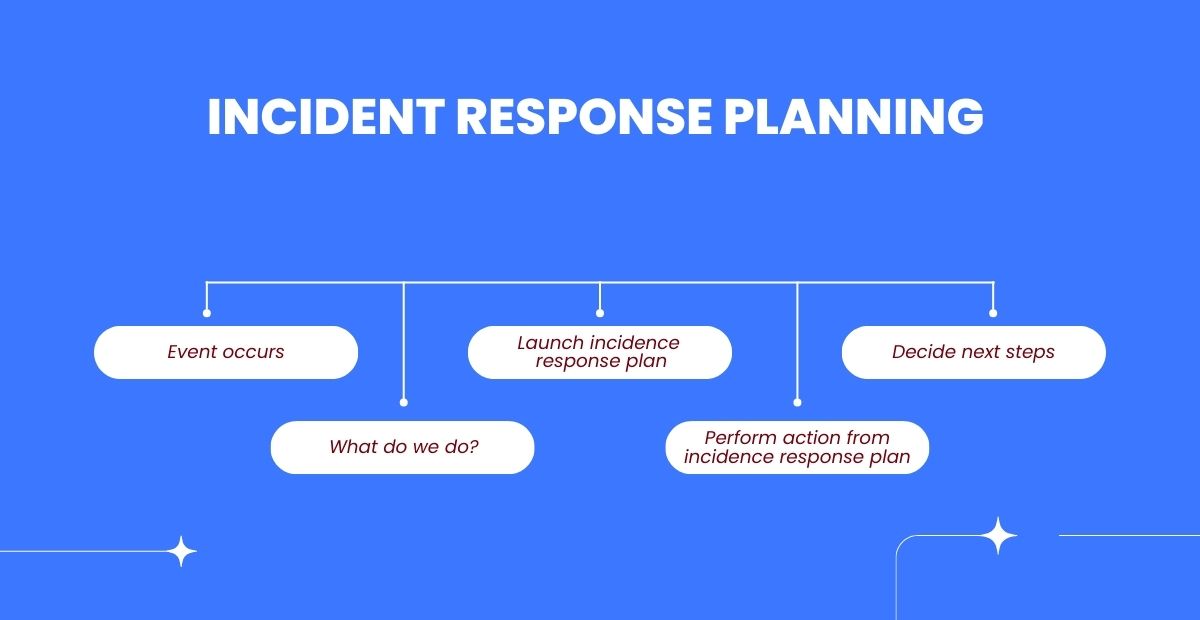
Doug Levin emphasises that planning for incidents is crucial: “You gotta be ready for anything. Develop an incident response plan to handle those security breaches like a pro.”
For example, here’s what you can do to create an effective incident response plan:
- Outline the steps to take when a security incident occurs. From identifying the breach to containing and resolving it, have a clear roadmap.
- Define roles and responsibilities. Assign specific tasks to individuals or teams so everyone knows their part in responding to the incident.
- Establish communication channels. Determine the best ways to communicate internally and externally during a security breach. This ensures that information flows efficiently and stakeholders are kept informed.
- Regularly test the plan’s effectiveness. Conduct mock drills or tabletop exercises to simulate security incidents and assess how well your response plan holds up.
Remember, your incident response plan should be a living document that evolves as new threats emerge.
That’s how you can effectively respond to security breaches. You can also minimise their impact on your edtech business.
You don’t want to miss this next part.
| Want to send fast and secure OTP and transactional messages to delight your students on WhatsApp? Get our WhatsApp messaging solution Today! |
How can you recover from a security breach on your education software?
So, you’ve taken all the necessary precautions to safeguard your digital classroom. But sometimes, despite our best efforts, security breaches can still occur.
Don’t fret. In the face of a breach, it’s time to roll up your sleeves and take action.
To combat and recover from a security breach in your digital classroom, follow these steps below:
- Stay calm and take a deep breath. Security breaches happen, but you can bounce back.
- Immediately isolate and contain the breach. Disconnect affected systems from the network to prevent further damage.
- Notify your internal team and relevant stakeholders about the breach. Communication is key to addressing the issue effectively.
- Engage your incident response team to lead the recovery efforts.
- Assess the extent of the breach and identify compromised data or systems. Understanding the scope helps prioritise recovery actions.
- Restore from backups or natural systems to regain functionality. Ensure that the restored data is secure and free from vulnerabilities.
- Patch and update all software and systems to prevent similar breaches in the future. Stay abreast with the latest security patches and fixes.
- Conduct a thorough post-incident analysis to learn from the breach. Identify weaknesses in your security measures and implement necessary improvements.
- Communicate with your users and stakeholders about the breach. Provide a piece of clear and transparent information about what happened.
- Review and enhance your security protocols. This includes access controls, encryption, and employee training to better protect against future breaches.
- Learn from the experience and continuously monitor and assess your systems’ security. This way, you can stay proactive in preventing and responding to future breaches.
That’s how you can recover from a security breach.
Now, what’s next?
Keeping your software users safe using SMS.
Discover the biggest benefits of bulk SMS for schools.
How do you keep your software users safe using SMS?
SMS (Short Message Service) is an effective tool for enhancing edtech security.
Let’s explore practical ways to leverage SMS to keep your software users safe.
1. OTP Two-factor authentication (2FA) via SMS
If you enable 2FA via SMS, you add an extra layer of protection.
Once users enter their credentials, a unique verification code is sent to their registered mobile number.
They must type in this code to gain access. This minimises the risk of unauthorised logins.
For example, imagine a student trying to log in to their online learning platform. After entering their username and password, they receive a text message with a code.
When they enter the code, they prove their identity and gain access to their account.
See the top 7 OTP service providers to secure your customers.
2. Password reset and account recovery
SMS is an effective way to verify and authenticate users during password reset and account recovery.
How? By sending verification codes to mobile numbers.
This ensures only the authorised user has regained access to their account.
3. Notification and alert system
SMS notifications and alerts are helpful when it comes to protecting personal data.
Let’s say a parent receives an SMS notification of an unusual login attempt on their child’s educational app. What do they do next?
They can take immediate action. They can contact the support team or reset their child’s password. This way, they can keep the account secure.
4. Important announcements and reminders
SMS is a reliable channel for sending timely updates, reminders and policy updates to your software users.
For example, a university administration sends out an SMS blast to all students. They remind students to review their privacy settings and adjust them according to their preferences.
This ensures that students stay informed and can actively manage their data privacy.
| SMSCountry is the best bulk SMS service to secure your students with fast OTP. Learn more about our SMS services. Get started or schedule a demo. |
Some security alerts SMS templates that’ll help keep your users safe
When keeping your users safe, timely and effective communication is vital.
Here are 10 SMS templates for security alerts that you can use to notify and guide your users in various situations.
Get inspired by these examples.
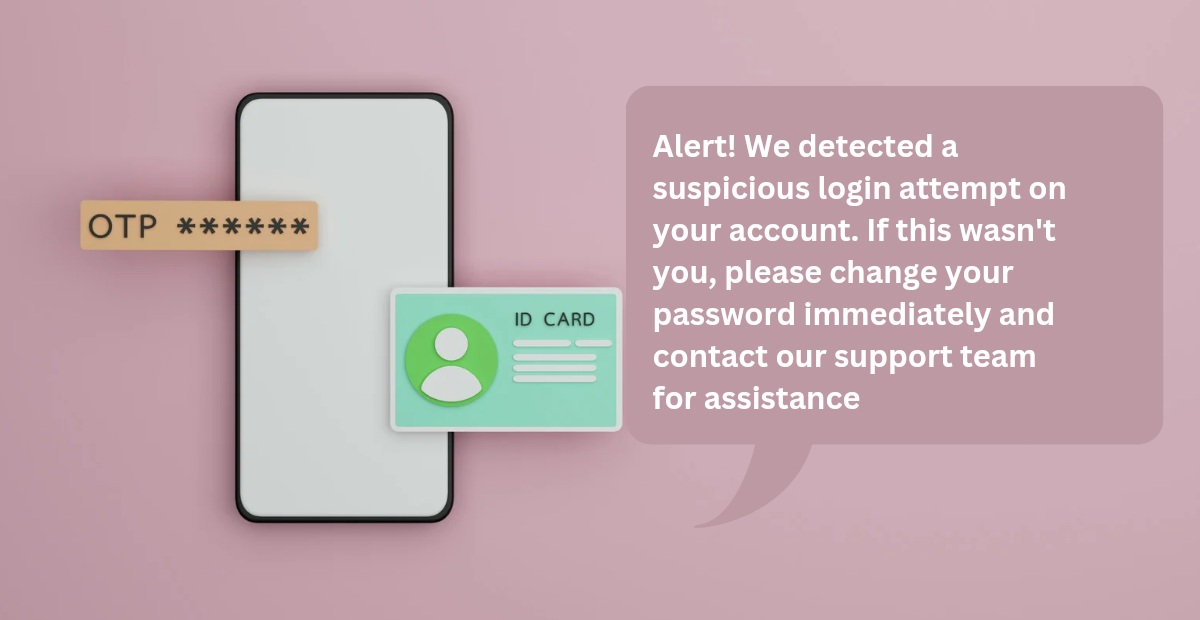
1. Suspicious login attempt SMS template
“Alert! We detected a suspicious login attempt on your account. If this wasn’t you, please change your password immediately and contact our support team for assistance.”
2. Password reset confirmation SMS template
“Your password has been successfully reset. If you did not initiate this action, please contact our support team immediately to secure your account.”
3. Account activity notification SMS template
“Hello [User], we noticed unusual account activity on your account. Please review your recent actions and update your security settings if needed. Contact our support if you need further assistance.”
4. Privacy policy update SMS template
“We’ve updated our privacy policy to protect your data better. To review the changes and manage your privacy settings, visit [website link].”
5. Important security reminder SMS template
“Attention! Your account security is important to us. Remember to use a strong, unique password and never share it with anyone. Stay safe!”
6. Two-factor authentication setup SMS template
“To add an additional layer of security, enable two-factor authentication (2FA). Go to your account settings and follow the instructions to set it up. Protect your account!”
“An unknown device was used to access your account. If this wasn’t you, please secure your account by changing your password and enabling 2FA. Stay vigilant.”
8. Phishing awareness SMS template
“Beware of phishing scams! Avoid clicking on suspicious links or providing personal information. Remember, we will never request your password via SMS or email.”
9. Data breach notification SMS template
“We regret to inform you that a data breach occurred. We are actively investigating the situation and taking steps to protect your information. More details will follow soon.”
10. Account lockout warning SMS template
“Your account is locked temporarily due to multiple failed login attempts. To unlock your account, kindly follow the instructions provided in the email we sent.”
Edu SMS best practices for the most effective results
You now have all the SMS templates to inform your students and teachers about data security.
But to get effective results, you must follow some best practices.
Here are the SMS best practices you can take note of:
- Keep it concise and to the point: Short and sweet messages are the way to go. No one wants to read an essay on their phone.
- Use a friendly and approachable tone: Let your personality shine through. Be warm and engaging to establish a connection with your users.
- Personalise when possible: Address your users by name for a more personalised touch. It shows that you value their individuality.
- Include clear instructions: Ensure your message includes actionable steps or directions. Tell them exactly what to do or where to find more information.
- Optimise timing: Send your SMS at appropriate times to maximise open rates. Avoid late-night or early-morning interruptions. Timing is everything.
- Respect privacy: Always prioritise privacy and obtain proper consent before sending SMS messages. Your users’ trust should be your top priority.
- Provide opt-out options: Offer an easy way to opt out of receiving further SMS communications.
- Monitor and analyse results: Keep track of SMS engagement metrics. The metrics include open rates and click-through rates. Analyse the results to refine your SMS strategy over time.
Secure your digital classroom with SMSCountry
There you have it. The expert tips and practical strategies you can apply to safeguard your digital classroom’s data and privacy.
But what’s the next step to ensure seamless communication and effective cybersecurity alerts?
Use SMSCountry, your trusted SMS partner.
SMSCountry is a reliable and cost-efficient SMS platform and API. It offers robust solutions, including OTP SMS services.
With SMSCountry, you can inform your students and teachers about critical cybersecurity alerts.
Schedule a FREE demo to see how we can help you with your edtech security today.